Thème Réseau et sécurité
Présentation
- La conception de protocoles de communicationes réseaux de communicationcouvrnt à la fois les technologies de courte et longue portée. Parmi les problématiques explorées, l’allocation des ressources et la gestion d’interférences dans des réseaux LoRaWAN, Wi-Fi, cellulaires et satellitaires, ainsi que l’interopérabilité entre différentes technologies de réseau, visant à créer des infrastructures de communication plus robustes et flexibles. L’optimisation dynamique des performances des réseaux devient de plus en plus cruciale avec la complexification et la densification des réseaux. Dans ce contexte, une partie de nos solutions repose sur es modèles d’Intelligence Artificielle (IA) qui permettent d’optimiser dynamiquement les performances des réseaux, en améliorant la gestion des ressources et en réduisant les interférences. Ces contributions s'adaptent aux besoins des applications allant de la surveillance environnementale aux cas d'usage industriels.
 |
 |
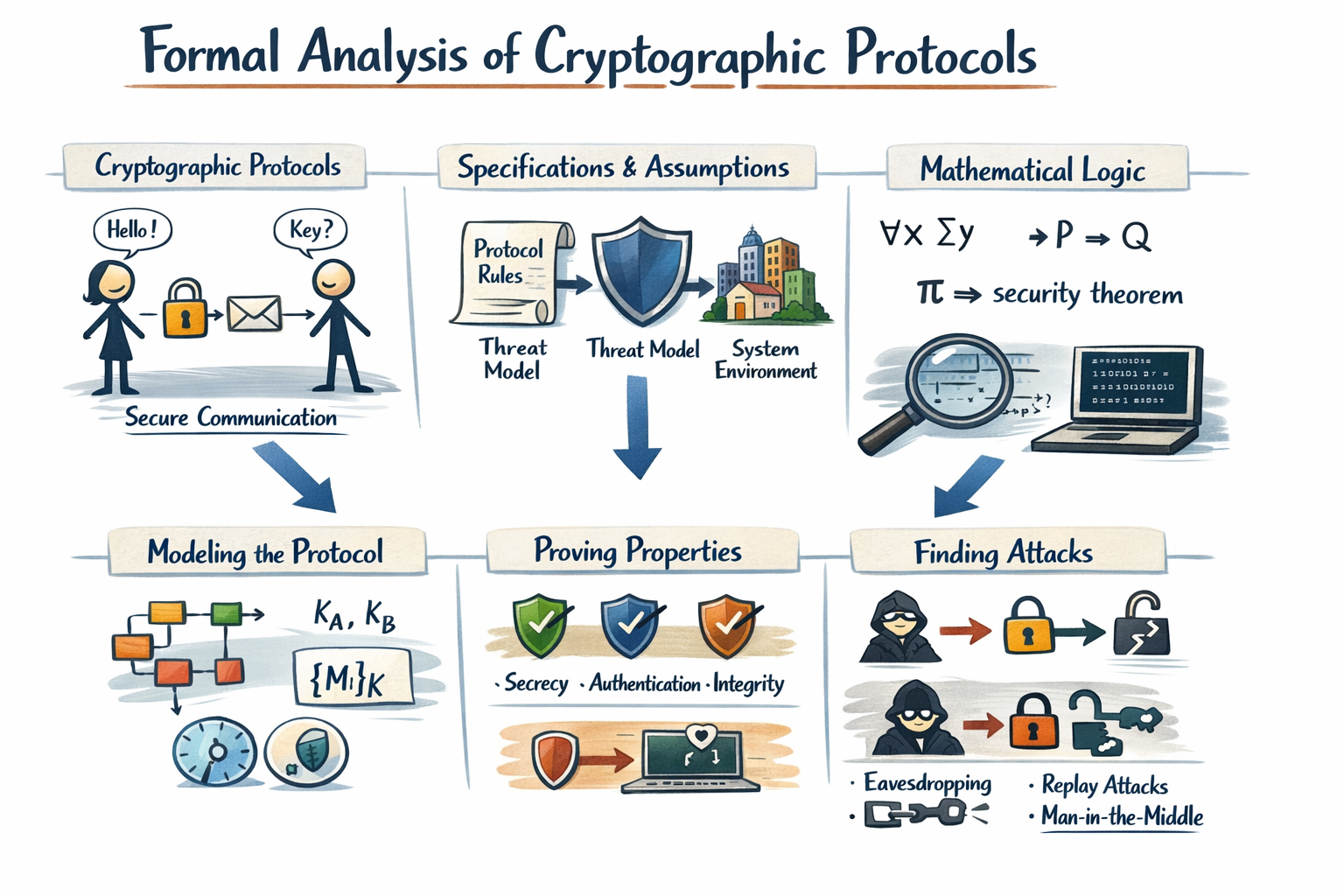
- La sécurisation P
 |
 |
Enfin, en outre ces trois activités structurantes, le thème RS entretient également plusieurs travaux connexes et en collaboration avec d'autres équipes et structures de recherche. Dans le cadre d'une collaboration avec l'Institut Pascal, nous travaillons sur l'implémentation de réseaux de neurones profonds sur des architectures FPGA. Ces travaux impliquent une forte dimension d'optimisation à la fois en termes de performances, mais également en termes d'espace pris sur le FPGA. Un second axe de recherche se focalise sur la sécurité des architectures LLM complexes (impliquant des pipelines RAG, des agents et du fine-tuning) dans le cadre d'une collaboration inter-thèmes avec le thème DSI de l'axe SIC. Cette collaboration est structurée autour de la Chaire Mécénale Utilisation Fiable et de Confiance des LLMs. Enfin, un troisième axe s'intéresse aux preuves à divulgation nulle de connaissance (zero-knowledge proofs) basées sur des objets physiques (jeux de cartes, balances de Roberval). Ces activités en collaboration avec l'Université Electro-Technique de Tokyo au Japon permettent d'agir en complément des primitives cryptographiques dans des environnements où l'informatique n'est pas considérée, tels que les élections avec urne et bulletins.
Nous organisons un séminaire mensuel : https://sancy.iut.uca.fr/~durand/seminaire/
Actualités
Dernières Publications
Sanitizable Signatures with Different Admissibility Policies for Multiple Sanitizers
ACM Asia Conference on Computer and Communications Security (ASIA CCS '26)
Quentin Bramas, Stéphane Devismes, Anaïs Durand, Pascal Lafourcade, Anissa Lamani - 14 janvier 2026
77 Shades of Grey
Gwendoline Hochet Derévianckine, Alexandre Guitton, Oana Iova, Baozhu Ning, Fabrice Valois - 19 novembre 2025
Hate or Love in the 2.4 GHz ISM band: The Story of LoRa® and IEEE 802.11g
ACM Transactions on Internet of Things
Mariem Zayene, Oussama Habachi, Gérard Chalhoub - 18 novembre 2025
Toward hyper-adaptive AI-enabled 6G networks for energy efficiency: techniques, classifications and tradeoffs
Zoé Lagache, Pierre-Henri Thevenon, Maxime Puys, Oum-El-Kheir Aktouf - 12 novembre 2025
Dissecting Mirai : Spatio-Sequential Analysis and Restoration Strategies Using MITRE ATT&CK and D3FEND
30th Nordic Conference on Secure IT Systems (NordSec)
Quentin Bramas, Pascal Lafourcade, Stéphane Devismes - 1 novembre 2025
Infinite grid exploration with synchronous myopic robots without chirality
Discrete Applied Mathematics
Oussama Habachi - 27 octobre 2025
Joint Power Control and User Assignment in RIS-based NOMA: A Multi-kernel Neural Network Approach
MSWIM'25 - 27th International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems
Tengfei An, Gewu Bu, Maria Potop-Butucaru, Bilel Zaghdoudi - 22 octobre 2025
Randomness is good enough in DAG-based Federated Learning
Pascal Lafourcade, Elsa Lopez Perez, Charles Olivier-Anclin, Cristina Onete, Clément Papon, Mališa Vučinić - 22 septembre 2025
Fine-grained, privacy-augmenting LI-compliance in the LAKE standard - Extended version
ESORICS 2025 - 30th European Symposium on Research in Computer Security
Lalie Arnoud, Zoé Lagache, Pierre-Henri Thevenon, Aloïs Champenois, Victor Breux, Maxime Puys, Éric Gaussier, Oum-El-Kheir Aktouf - 22 septembre 2025
HENDRICS: A Hardware-in-the-Loop Testbed for Enhanced Intrusion Detection, Response and Recovery of Industrial Control Systems
30th European Symposium on Research in Computer Security (ESORICS 2025), Workshop on Assessment with New methodologies, Unified Benchmarks, and environments, of Intrusion detection and response Systems (ANUBIS)
Toutes les publis se trouvent ici
Projets
Equipe
Responsables
Enseignants-Chercheurs
- BATTA Mohamed
- BU Gewu
- CHALHOUB Gérard
- DELOBEL François
- DE VAULX Christophe
- DURAND Anaïs
- EL RACHKIDY Nancy
- FREITAS Antonio
- GUITTON Alexandre
- HABACHI Oussama
- LAFOURCADE Pascal
- LI Jian-Jin
- MESNARD Emmanuel
- MIGDAL Denis
- OLIVIER-ANCLIN Charles
- PUYS Maxime
Professeurs émérites
Post-docs
Doctorants
- ADJE Karidja Dominique
- ALLABWANI Osama
- CHAGNON Dorine
- CHEBBI Samar
- DURECU Florent
- MUKUND Shrey
- NAHNAH Oussama
- NAMA NYAM Guy Anthony
- NOUYEP NOUNDJIO Steve Durand
- ZHAO Yan